
This document outlines the setup process for integrating SAML-based Single Sign-On (SSO) with Abacus.AI using Microsoft Entra ID (formerly Azure AD). It also includes best practices, security requirements, and answers to commonly asked enterprise questions.
SAML-based SSO allows organizations to securely authenticate users into Abacus.AI using their existing identity provider. This document focuses on setting up SAML integration with Microsoft Entra ID.
Important Notes:
- Currently, we only support IDP-initiated SAML. This means you will log in from Microsoft Entra (formerly Azure AD).
- Clicking the "Sign in with Microsoft" button triggers OAuth-based SSO instead of SAML.
If you do not wish to use SAML-based SSO for Microsft Entra ID, please see the instructions here.
We only support IDP(entra) initiated login now.
Confirm the Abacus.AI organization you want to sign into:
Set the following configuration:
https://<subdomain>.abacus.ai https://abacus.ai/api/samlSignInhttps://<subdomain>.abacus.aiWe assume you will gate on who can be added as platform users to have more permissions.user.userprincipalname. We use the email address to uniquely identify users, and userprincipalname is more consistent.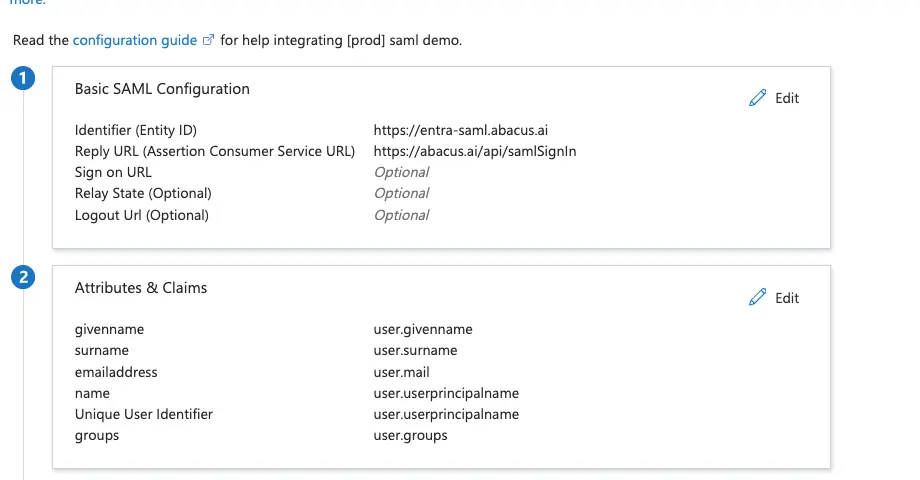
[Optional] Create other desired attributes or claims, such as a groups claim:
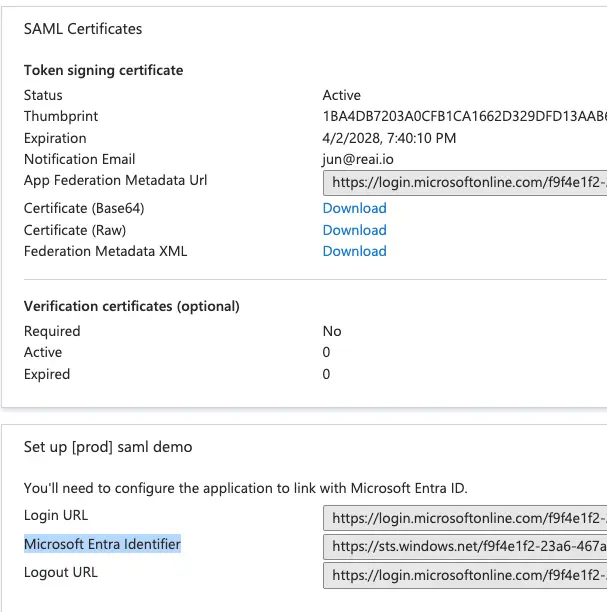
Share the following information with Abacus.AI at connectors@abacus.ai to complete the setup:
Create the following custom roles in Entra ID. (You should have a P1 or P2 licence to create custom roles).
After these roles are created, the next step is to assign them to the users or groups. Users who are assigned roles should be able to see apps in My Apps.
Note: Users will be created in Abacus.AI and roles will be updated in Abacus.AI dashboard when they try to login to Abacus.AI.
For enabling role and group management via SAML—rather than using our built-in groups and roles management—please contact us or email us at connectors@abacus.ai .
Invalid Audience URI (Entity ID mismatch):
- Error: "Audience URI is invalid" or "Invalid recipient."
- Cause: The audience or Entity ID in your IdP is incorrect.
- Fix: Match exactly with https://<subdomain>.abacus.ai. Watch for typos or slashes.
Missing or Mismatched Attributes:
- Error: "Invalid login" or user isn’t created via JIT provisioning.
- Cause: Required attributes like email, firstName, or lastName are missing.
- Fix: Ensure these are mapped and correctly named in IdP settings.
Invalid or Expired x509 Certificate:
- Error: "Signature validation failed" or "Untrusted certificate."
- Cause: Expired or mismatched certificate.
- Fix: Renew the certificate and share the updated one with support.
Debugging Tip:
- Use browser extensions like SAML-tracer to inspect assertions, detect missing attributes, or identify signature
issues.
https://<subdomain>.abacus.ai . If you need a different page, please contact us at support@abacus.ai. connectors@abacus.ai.